CLOUD SECURITY - THE ABC OF ZERO TRUST AND INTERVIEW WITH CLOUD LEADER "SWAPNIL SHAH"
The ABC of Zero Trust and Interview with Cloud Leader “Swapnil Shah”
Introduction:
Many cybersecurity products, solutions and services are touting Zero Trust, Zero Trust
security model, Zero Trust Architecture, etc. The purpose of this article is to help readers
understand in simple form what is Zero Trust, how is it related to Zero Trust Architecture.
Finally this article wraps up with an Interview with Cloud Leader “Swapnil Shah” who will
share insights into the new Norm for clients adopting Cloud and adopting Zero Trust in
securing their assets in Cloud.
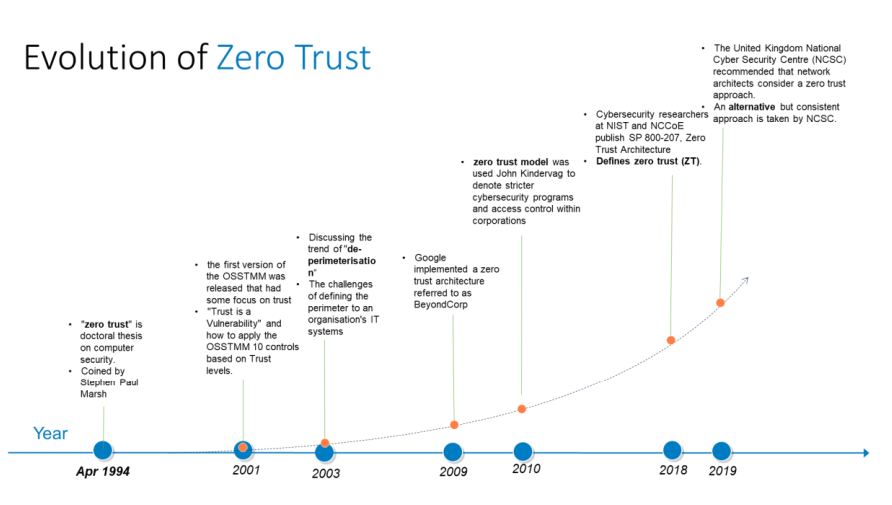
(A) Evolution of Zero Trust
To understand Zero Trust, we first look at the history of Zero Trust. The term “zero trust”
started as a doctoral thesis by Stephen Paul Marsh in 1994. He believes that the concept
of trust transcends human factors such as morality, ethics, lawfulness, justice, and
judgement. Thereafter the concept of “zero trust” has been discussed. In 2009 Google
implemented a zero-trust architecture referred to as BeyondCorp which consider both
internal networks and external networks to be completely untrusted.
In 2018, US cybersecurity researchers at NIST and NCCoE publish Zero Trust Architecture
(SP 800-207). They define Zero Trust (ZT) as a collection of concepts and ideas designed
to reduce the uncertainty in enforcing accurate, per-request access decisions in
information systems and services in the face of a network viewed as compromised. In
2019 the United Kingdom National Cyber Security Centre (NCSC) stressed the important
of considering a zero trust approach for new IT deployment especially for cloud services.
The following diagram shows the timeline of Zero Trust:
(B) What is Zero Trust (ZT) security model and Zero Trust architecture (ZTA)
NIST defines that Zero Trust is not a single architecture but a set of guiding principles for
workflow, system design and operations that can be used to improve the security
posture of any classification or sensitivity level.
Zero trust architecture (ZTA) is a plan where enterprise uses zero trust concepts and
implementing it in its environment that includes network infrastructure (physical and
virtual) and operational policies. Oftentimes the term ZTA is also known as follows:
- Zero Trust architecture (ZTA)
- Zero Trust security model
- Zero Trust network architecture
- Zero Trust network access (ZTNA)
- Perimeterless security
The aim of ZTA is to prevent unauthorized access to data and services and to make the access control enforcement as granular as possible. This focus of ZTA is:
- Enforce authentication, authorization, and
- Reduce implicit trust zones without impacting service availability and delays in authentication mechanisms.
- Access rules are made as granular and enforcing least privileges principle.
In today’s market ZTA concept is commonly known as “never trust, always verify,” which means that devices should not be trusted by default whether they are in trust or untrusted network.
(C) Basic Rules of Zero Trust
A Zero Trust Architecture is designed and deployed with adherence to the following basic rules. These rules are ideal goals and it must be acknowledged that not rules can be fully implemented in the ZTA.
- All data sources and computing services are considered resources.
- All communication to be secured regardless of network location (trusted or untrusted location)
- Access to individual enterprise resources is granted on a per-session basis.
- Access to resources is determined by dynamic policy.
- Enterprise monitors and measures the integrity and security posture of all owned and associated assets.
- All resource authentication and authorization are dynamic and strictly enforced before access is allowed.
- The enterprise collects as much information as possible about the current state of assets, network infrastructure and communications and uses it to improve its security posture
Interview with Cloud Leader “Swapnil Shah”
In this section I had the privileged to interview Cloud Leader “Swapnil Shah” who share insights into client adopting cloud, viewpoints on cloud security and Zero Trust.
1. What is the new Norm for clients adopting Cloud?
Cloud adoption is mainstream for some time now and Cloud First or Cloud Only strategies are commonplace across most enterprises across all leading markets. The adoption of the Cloud is key, and sometimes even synonymous, with Digital Transformation initiatives. It is common knowledge that Cloud adoption is the underlying key enabler for innumerable business use cases like telemedicine and connected health devices, smart grids for utilities, financial risk analysis, edge computing on 5G, IoT-enabled shop floors, contactless retail, drone-powered delivery, networks on the Cloud, autonomous and driverless cars, etc. Nevertheless, Cloud computing continued to languish as a mere technology upgrade project within most enterprises. The focus of enterprises is now shifting to how to innovate and differentiate by leveraging a wide range of cloud-native offerings and industry cloud solutions available from hyperscalers and various eco-system partners. The current pandemic has inserted an additional dimension of unpredictability and has accelerated the pace of digital transformation across industries. Multi-year project timelines are being compressed, and project requirements are being dramatically altered on-the-fly. Enterprises are now at a tipping point, for having to super-scale their Cloud-powered Digital transformation efforts.
2. Accelerated adoption of cloud combined with complex integration of eco-system, hybrid working environments is the new norm which poses interesting challenges to IT executives not only from architecture & technology side but also from culture and security perspective as well. What are your viewpoints on Cloud security?
In traditional IT world, IT security was completely owned and controlled by various teams within IT or ISG groups. Cloud Security is a Shared Responsibility now shared between enterprises IT teams, Cloud provider and any eco-system partners involved in the solution. Modern cloud adoption presents very challenging security realities due to below key elements:
- automated CI/CD methods
- distributed serverless architectures
- and ephemeral assets like Functions as a Service and containers
- no clear perimeter boundaries
- api adoption explosion
This creates unique challenges like below which enterprise security team needs to assess on continuous basis
- complex environments with complex integration points outside enterprise perimeter
- increased attack surface
- lack of visibility & tracking
- complex data flow patterns between on prem, hybrid cloud (IaaS/PaaS) & SaaS based applications and users spread everywhere
- everchanging workloads
3. How should customers adopt Zero Trust in securing their assets in Cloud?
Basic guiding principles for Zero Trust in cloud security is not to automatically trust anyone or anything within or outside of the network and to authorize, inspect and secure everything. A Zero Trust approach extends throughout the entire digital estate and serves as an integrated security philosophy and end-to-end strategy. Enterprises as part of their cloud adoption journey should look at below Zero Trust based elements at a high level:
- Leverage cloud-delivered security measures where possible to implement Zero trust on cloud
- Granular, policy-based IAM and authentication controls across complex infrastructures: Reduce the attack surface area by limiting user access based on context.
- Zero-trust cloud network security: Controls across logically isolated networks and micro-segments
- Enforcement of virtual server protection policies and processes such as change management and software updates:
- Safeguarding all applications (and especially cloud-native distributed apps): E.g. leverage a next-generation web application firewall
- Enhanced data protection
- Threat intelligence that detects and remediates known and unknown threats in real-time
- Develop apps using Zero Trust principles
Biography: Alvin Tan

Alvin is a security practitioner certified in CISSP, CCSP and Azure. He has worked in the ICT industry for over 20+yrs. Alvin is experienced in several key technologies such as Data centres, Hybrid Cloud, International connectivity, Networks, Cloud Security, Information Security, Apps and Big Data solutions. He focused in helping enterprises creating competitive advantage through business transformation. He is a SIG member of AISP and a (ISC)² member.
Biography: Swapnil Shah

Swapnil Shah is Cloud executive with a passion for transitions and transformations in business and people. He is driven to empower clients to accelerate their digital transformation initiatives supported by technology and service transformation enabled by Cloud technologies. Swapnil holds a Bachelors Degree in Electronics Engineering. His career spans 23 years where he has played wide range of roles across Asia, UK, US and Australia across enterprise and telecom sector. He is also a very passionate and driven career & life coach who empowers IT, professionals & executives to successfully transition & transform their careers.